Website Information
The product uses weak credentials (such as a default key or hard-coded password) that can be calculated, derived, reused, or guessed by an attacker.
1 |
https://**********.DATA.GOV.MY/ |
[Risk Factors]
Technical Impact: Gain Privileges or Assume Identity
An attacker could easily guess user passwords and gain access admin/user accounts.
[Preface]
Default User Password
User ID : superuser , jasperadmin
Password : superuser , jasperadmin
Description : System-wide administrator , Administrator for the default organization
[Access Dashboard]
Unsurprisingly, I was able to access into the web (Public), which leads to injection vulnerabilities. The following process :
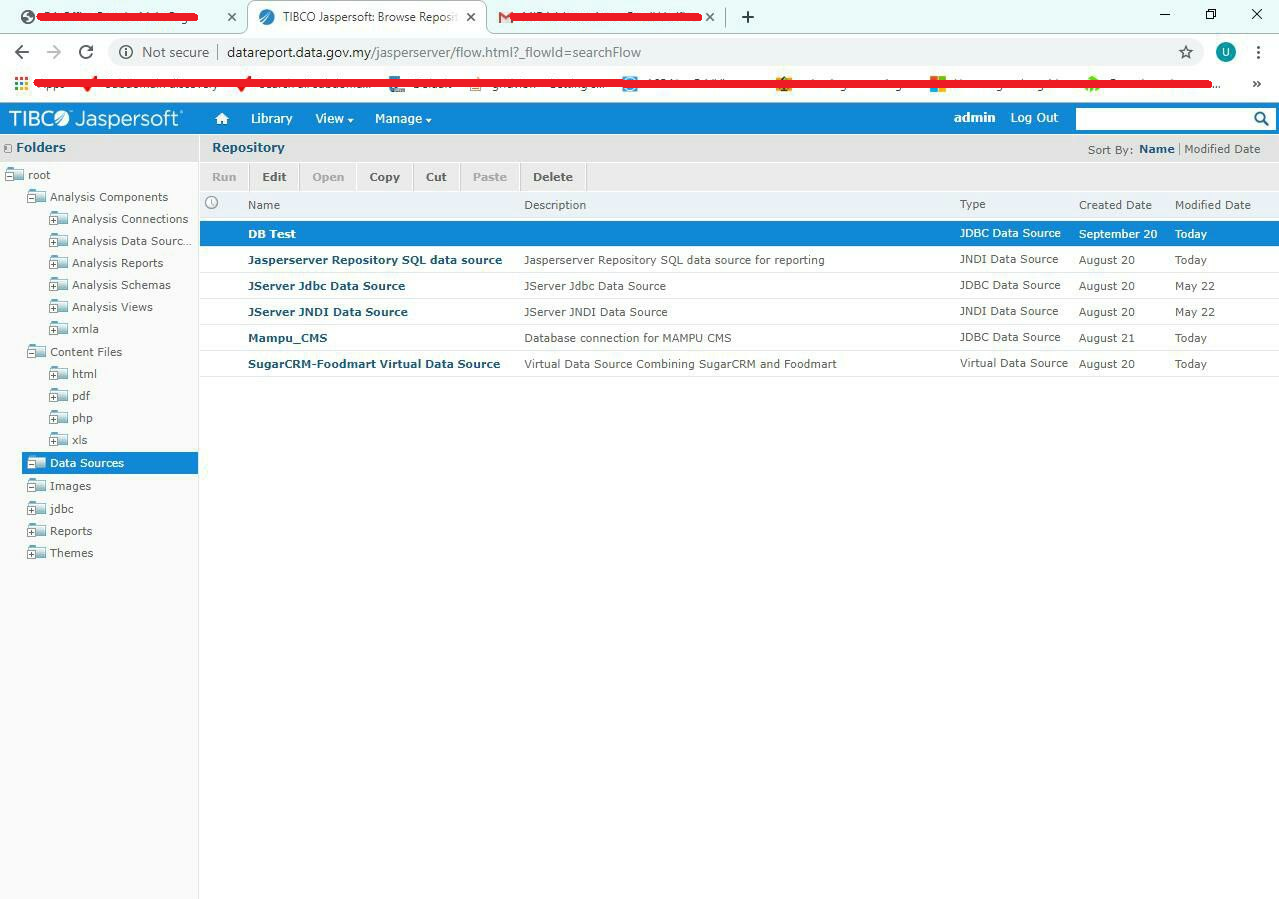
[JasperServer Login]
JasperServer Login Admin Dashboard Interface
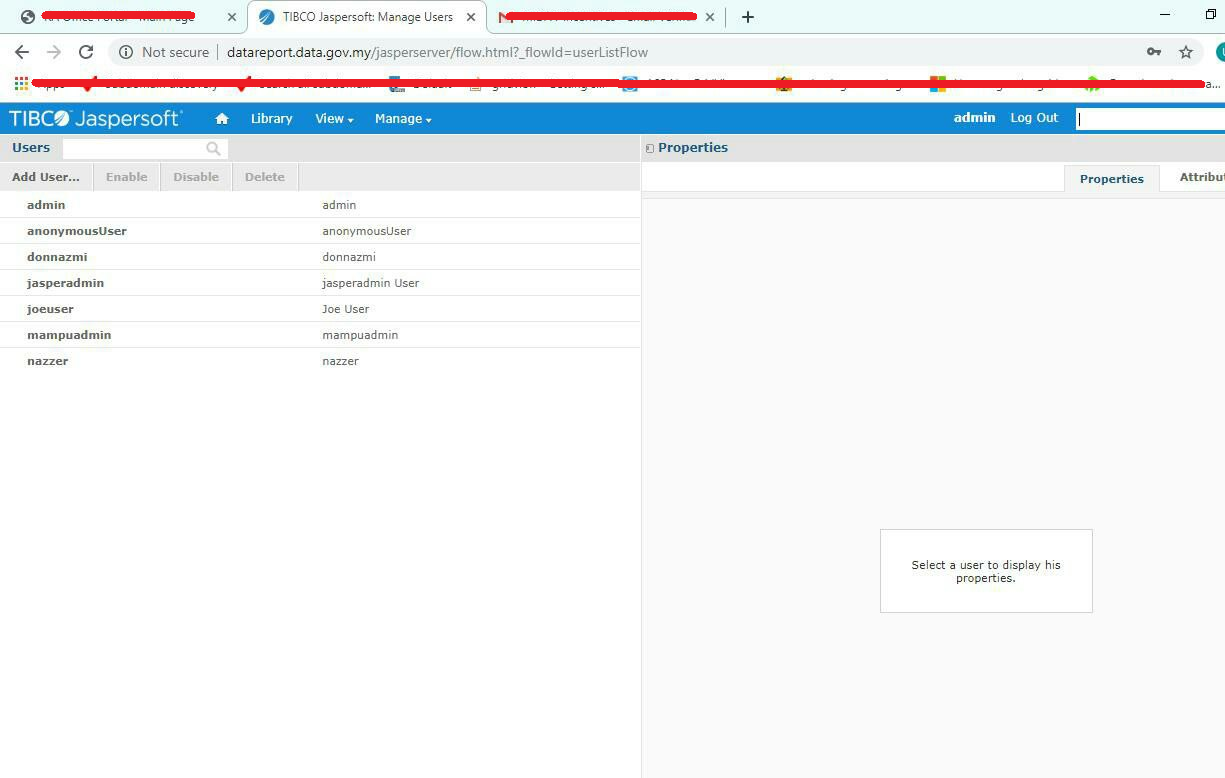
[JasperServer User]
JasperServer User List Dashboard Interface.
Unfortunately,I am able to create new admin/user account, client-side validation was applied due to Weak Default passwd CWE-1391 functionality allow attacker to login without authentication.
[Concluding]
Mission accomplished! Full Weak Default passwd CWE-1391 to get Access into thier system.
Since people have been asking, the bug had already been fixed.
[Affected Component]
Login functionality
[Has vendor confirmed or acknowledged the vulnerability?]
true
CWE-1393Sorry about my english, is so bad😅
If you have any questions or suggestions, make sure to hit me in any of these mediums or the comments.
Thanks for reading.
[DISCLAIMER]
This Vulnerability I've report on October 03, 2019Special thanks to Tuan Adzmely Mansor.