Anything u learned from the Blog just for research and educational purposes only Do not use the knowledge for illegal things.
[Risk Factors]
This exploit attacks a weak encryption implementation to discover the dialog handler key for vulnerable versions of Telerik UI for ASP.NET AJAX, then provides an encrypted link which gives access to a file manager, and arbitrary file upload (e.g. web shell) if remote file permissions allow. Works up to and including version 2017.1.118.
[Preface]
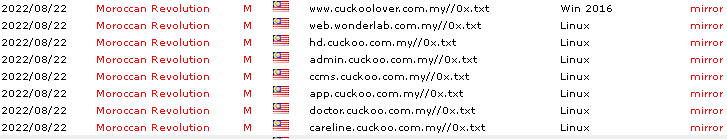
A couple of days ago, I was browsing Zone-H for checking Malaysian Website Defacecment activity, and I see that some Malaysian websites have been successfully hacked by the Moroccan Revolution Team. Immediately I wondered What Exploit they are use…Could I hack it?
Zone-h Cuckoo Web Defacemet.
[Getting Started]
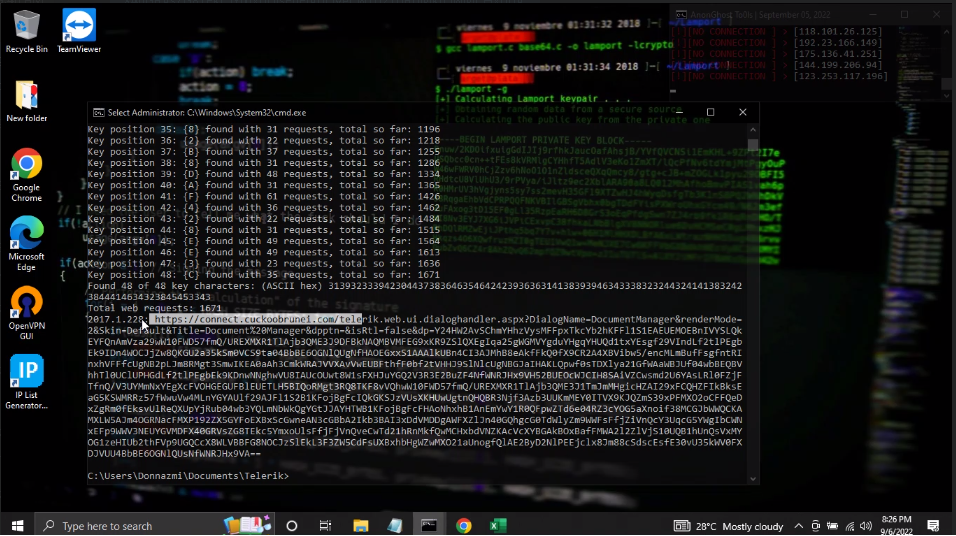
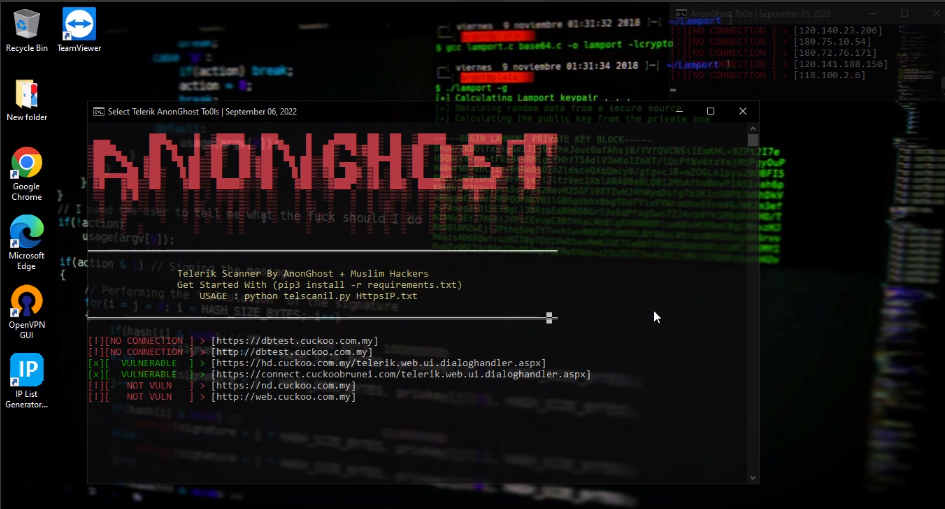
I randomly scan all the subdomains and right away jumped onto the research. and I found the Vulnerable CVE-2017-9248
Vulnerable Found :
➜ ~ .https://*****.cuckoo.com.my/Telerik.Web.UI.DialogHandler.aspx
➜ ~ .https://****.cuckoo.com.my/Telerik.Web.UI.DialogHandler.aspx
➜ ~ .https://**.cuckoo.com.my/Telerik.Web.UI.DialogHandler.aspx
➜ ~ .https://***.cuckoo.com.my/Telerik.Web.UI.DialogHandler.aspx
➜ ~ .https://co*****.cuckoobrunei.com/telerik.web.ui.dialoghandler.aspx
➜ ~ .https://h*.cuckoo.com.my/telerik.web.ui.dialoghandler.aspx
[Exploit]
Exploit Vulnerable Web.
[POC Video :]
[DISCLAIMER]
This issue has been reported to MyCert & improved by Cuckoo September 05, 2022 the bug had already been fixed..
Special thanks to MyCert Team , who helped throughout the process.
Sorry about my english, is so bad😅
If you have any questions or suggestions, make sure to hit me in any of these mediums or the comments.
Thanks for reading.