[Preface]
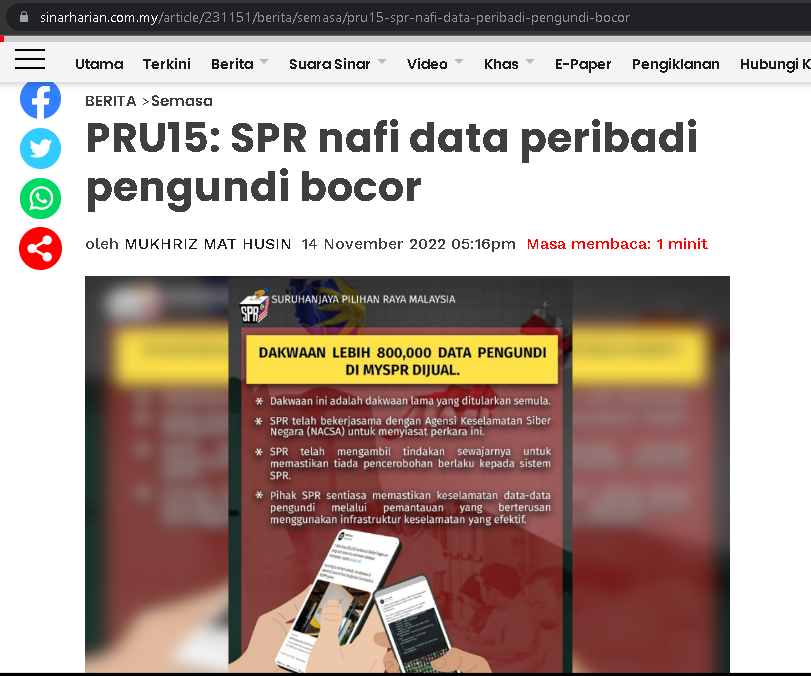
A few days ago, I was scrolling my Facebook and saw the Sinar Harian news about SPR data leakage, and so many news articles about Malaysian people's data being leaked and hacked,
As a registrant, I also need to be concerned about the security of my PRIVACY DATA.so I want to continue the research is it true that SPR can be leaked or can be hacked?
Sinar Harian News Link
Where suddenly I came across the SPR link found on google. website can register as a normal user I thought it could be an interesting challenge.., Immediately I wondered…Could It can be hacked?
[Getting Started]
I connected the website to my computer and right away jumped onto the research.
I started off with a good ol’ opened the website interfaces and my potential attack vectors.
1 |
https://*********.SPR.GOV.MY |
Unsurprisingly, looks like all we got to work with the web server. Off we go then.
Browsing to the website presents a login prompt and Register,and I Found something suspicious phpdebugbar on web page element. it made me wonder and made me want to click the link.
What makes me wonder more is that I don't need to login or register to click the link.
The following is a picture of the main display of the website and phpdebuger :
https://*********.SPR.GOV.MY/ Home Page
https://*********.SPR.GOV.MY/ phpdebugbar
[Hacking Time]
Initially, I was looking for potential input from clients when I came across a page register and login.
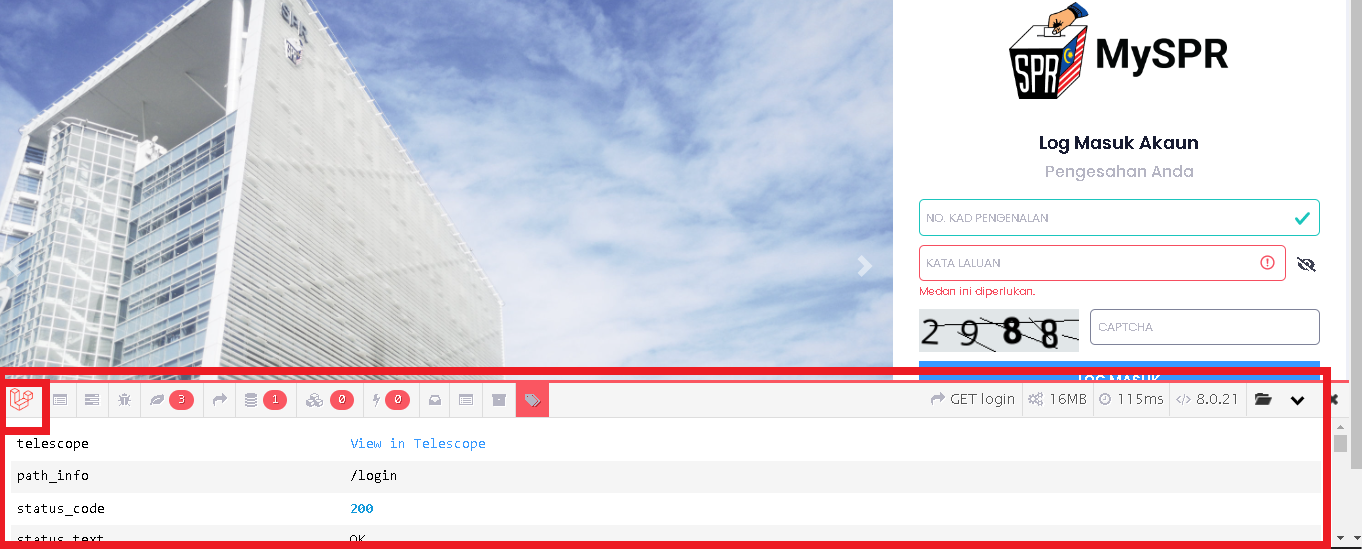
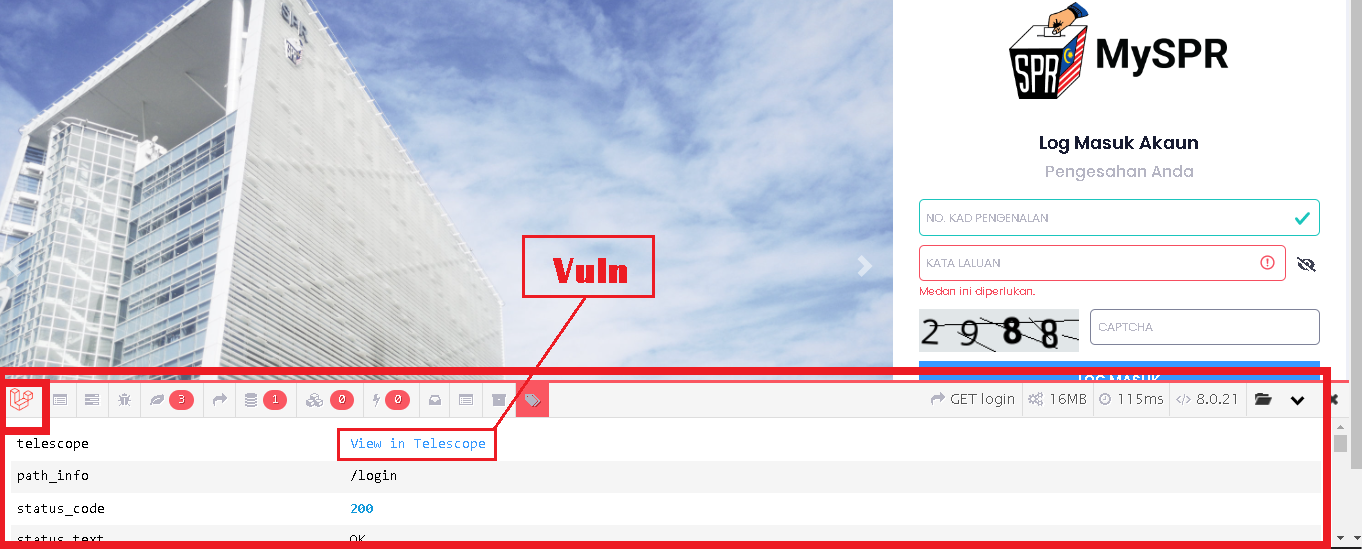
But I'm more interested in clicking the phpdebugbar link that has been provided publicly. and it is a Telescope
https://*********.SPR.GOV.MY/ View in Telescope
Unfortunately, I can access the Telescop view, it stores various sensitive data including Admin Login Usename Password.
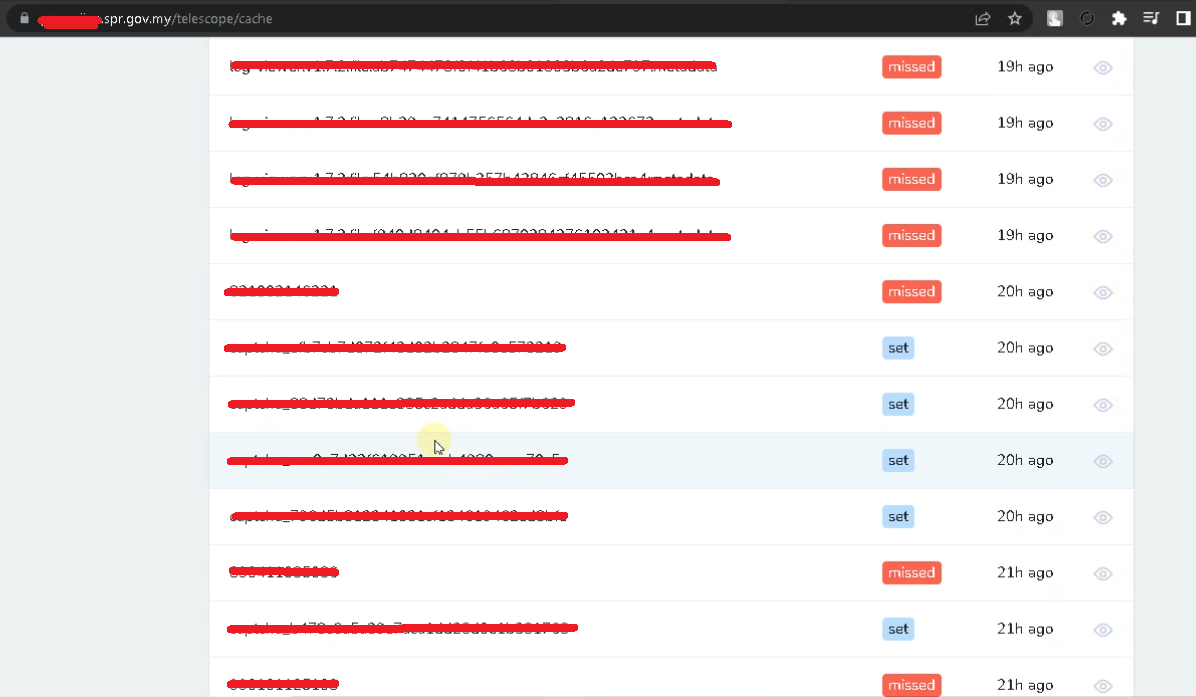
https://*********.SPR.GOV.MY/ Telescope Cache
I have found various accesses to enter the website as an administrator by pressing the Telescop display and in the "cache" section and in this section the administrator's login data is stored.
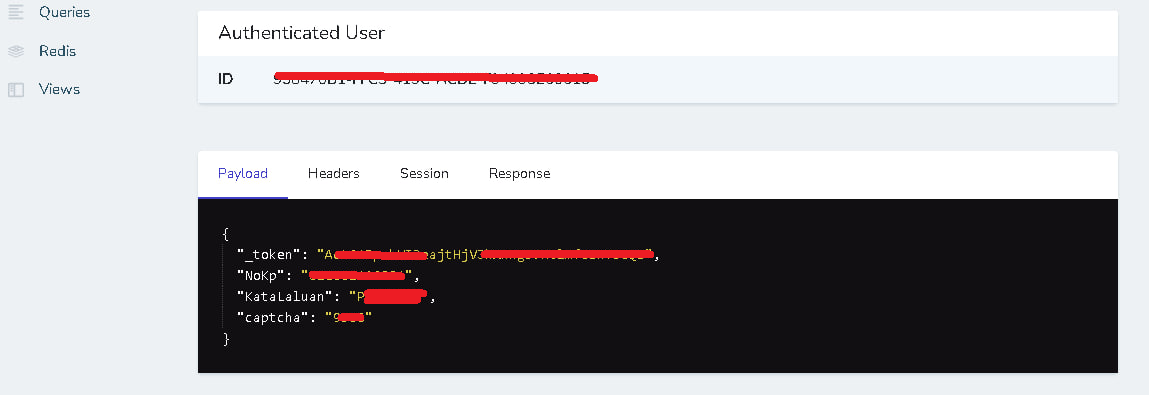
https://*********.SPR.GOV.MY/ Telescope Cache Sensitive Data
https://*********.SPR.GOV.MY/ Telescope Cache Sensitive Data
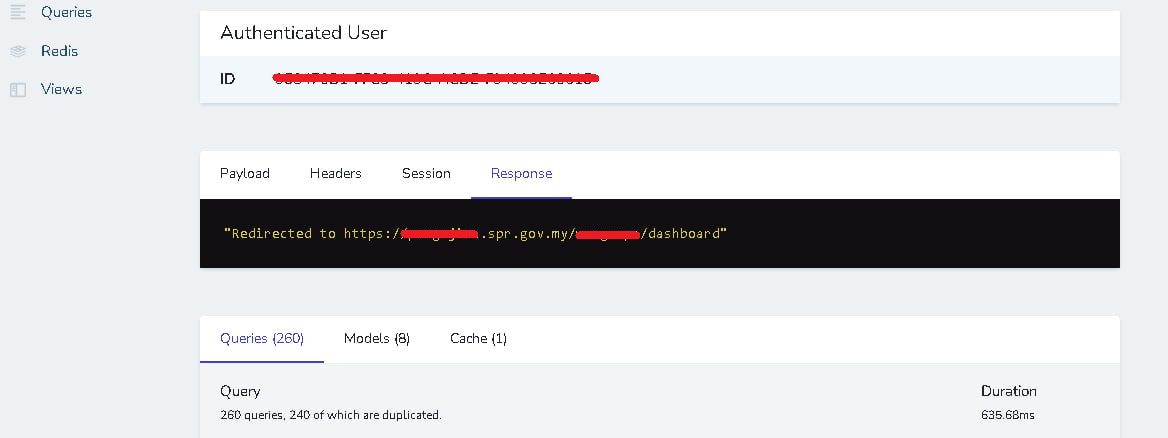
without wasting time I log into the admin system using data taken from Telescope view "cache"
https://*********.SPR.GOV.MY/ SPR Admin
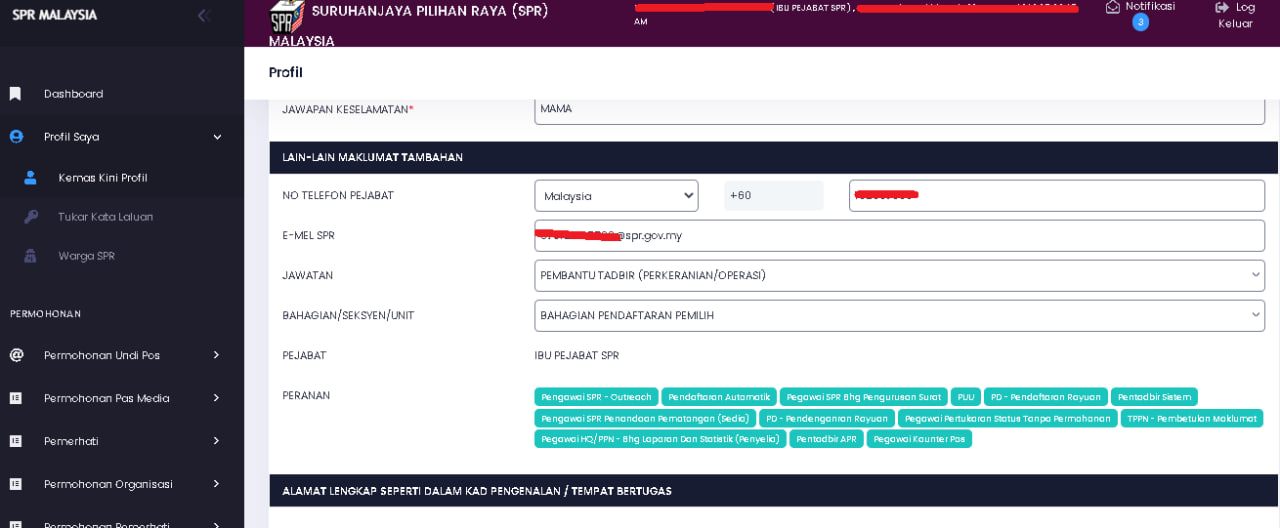
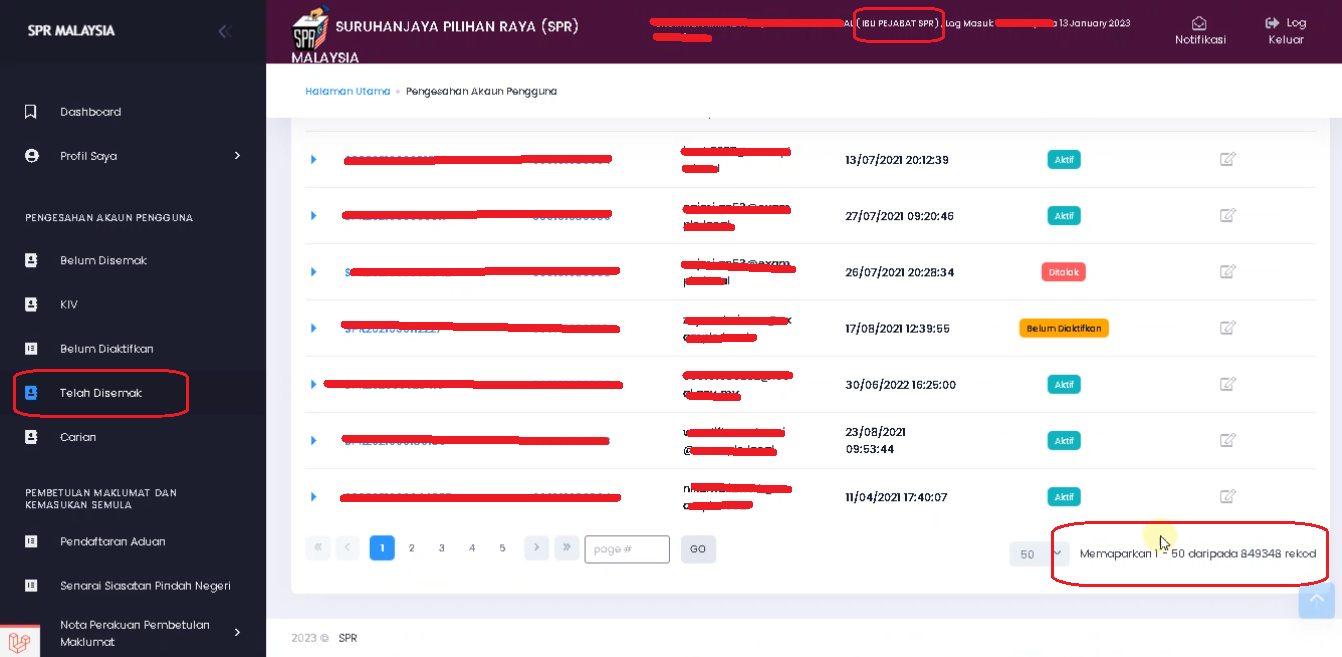
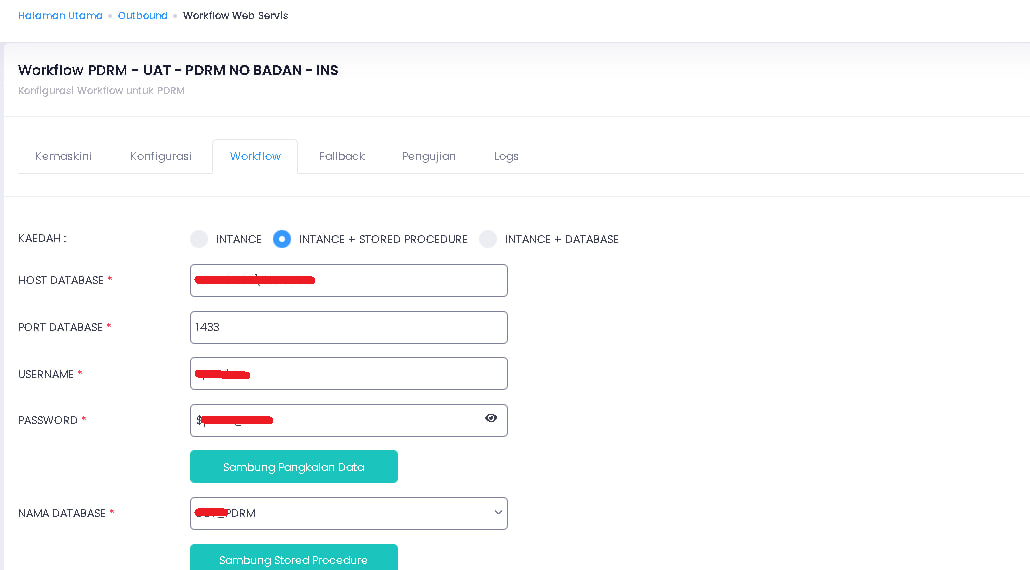
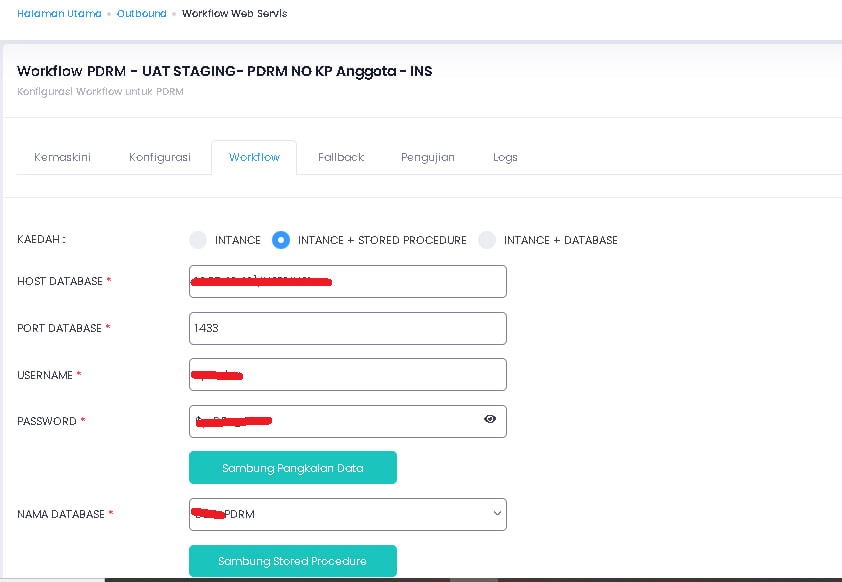
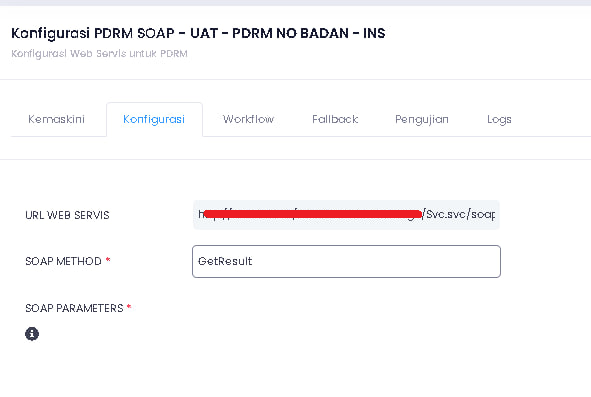
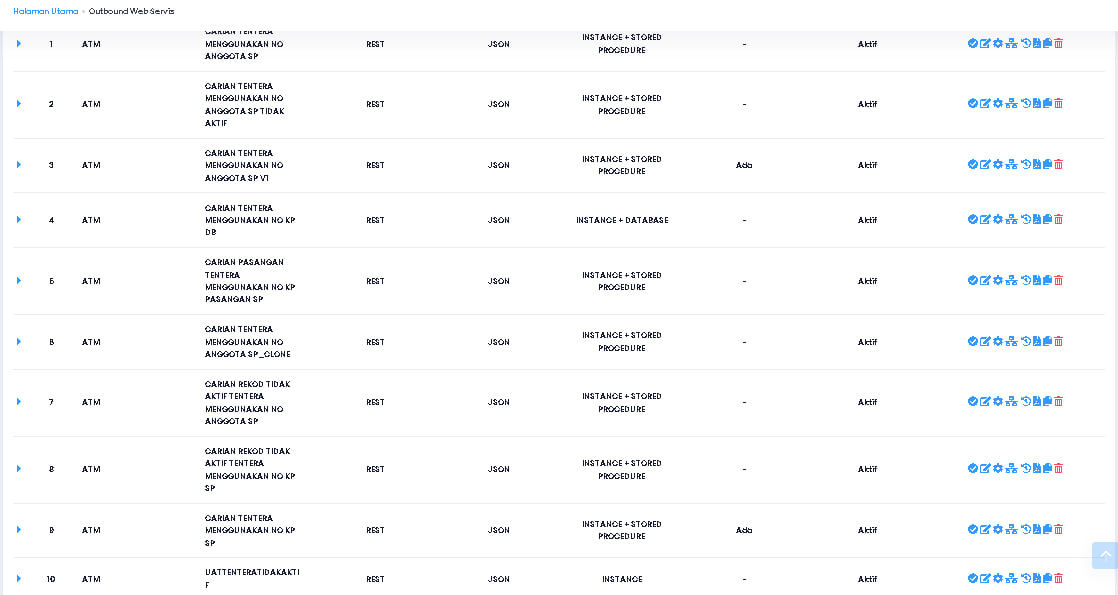
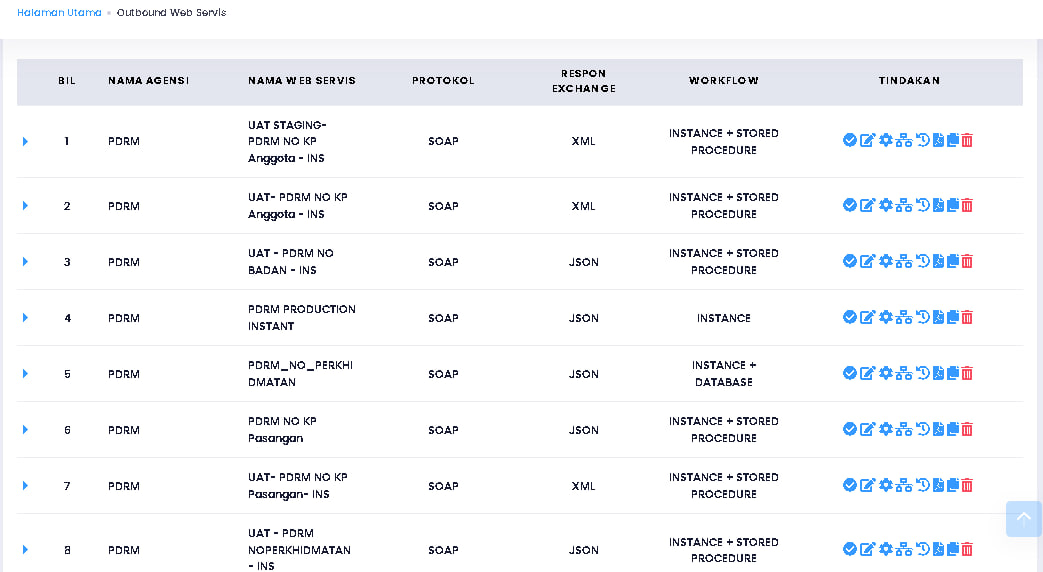
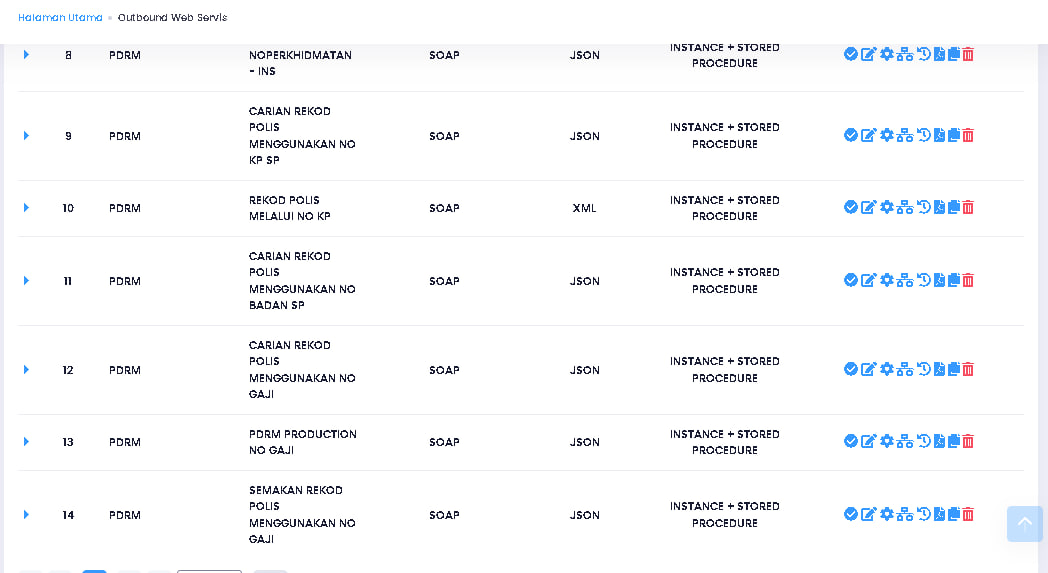
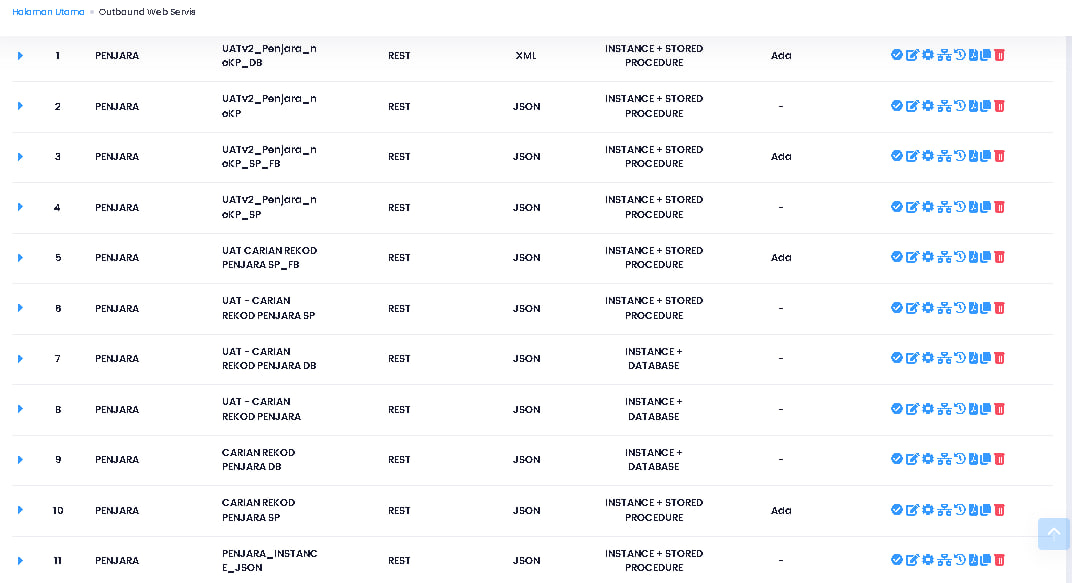
More surprising and unexpected, I can see all registered users more than 10 million users excluding others. I also had time to see the configuration of the JPN PDRM PRISON ATM database
https://*********.SPR.GOV.MY/ SPR Userdata
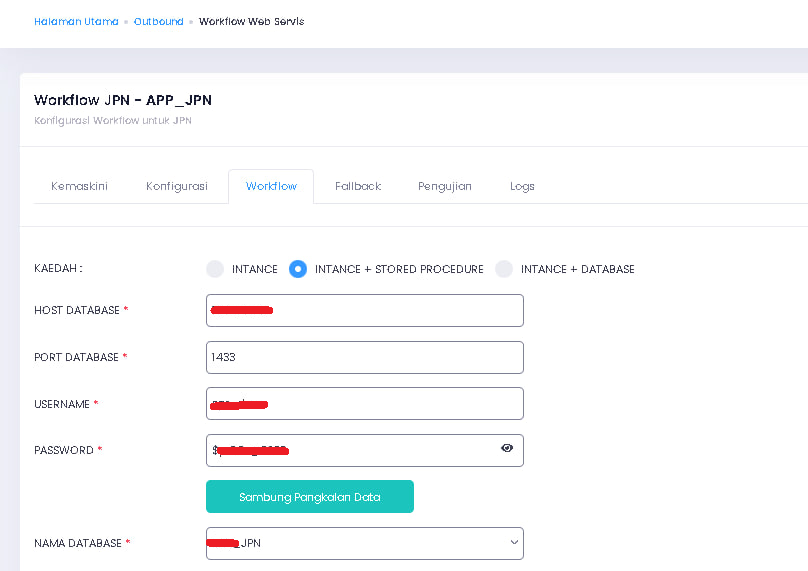
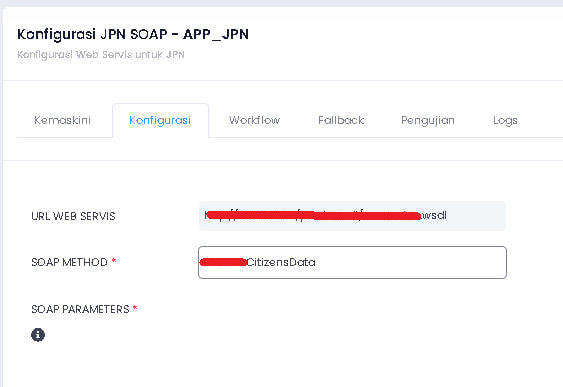
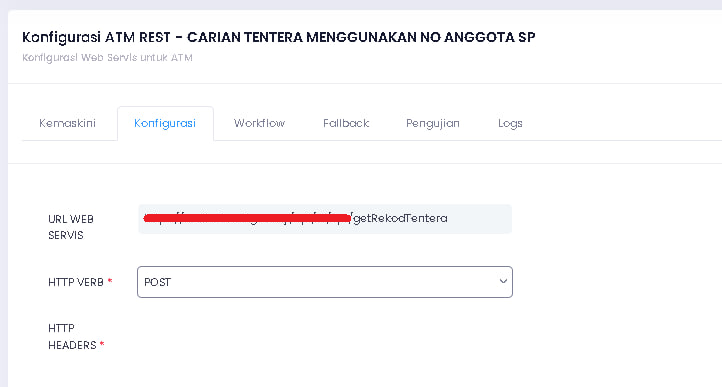
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
https://*********.SPR.GOV.MY/ Webservice Database
[Remediation]
The web application uses Laravel framework. Laravel Telescope is enabled and accessible.
In production environment, it leads to disclosure of sensitive information about the web application.
Disable the Telescope or restrict access to it
[Classification]
CWE-200 CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:L/I:N/A:N
[Affected Component]
Telescope
[Has vendor confirmed or acknowledged the vulnerability?]
true
Ref :
[Concluding]
Mission accomplished! to get Access into thier system.
Since people have been asking, the bug had already been fixed.CWE-200
[DISCLAIMER]
This Bug I've report to MyCert Team January 13 2023
Anything u learned from the Blog just for research and educational purposes only Do not use the knowledge for illegal things.
Sorry about my english, is so bad😅
If you have any questions or suggestions, make sure to hit me in any of these mediums or the comments.
Thanks for reading.